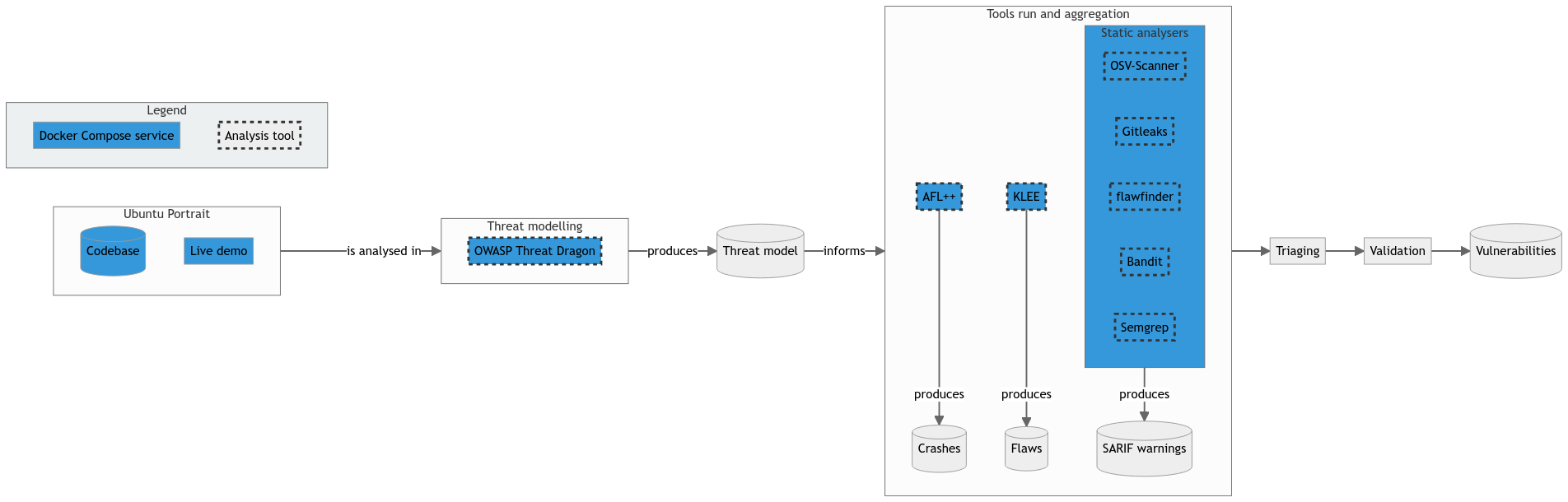
Analysis infrastructure
Tooling
The tools that will be used during the workshop are:
- OWASP Threat Dragon for modelling the cyberthreats for a given application;
- Gitleaks for scanning a Git repository for leaked secrets;
- OSV-Scanner for scanning dependencies for vulnerabilities;
- flawfinder for statically analysing C code to find security concerns;
- Bandit for statically analysing Python code to find security concerns;
- Semgrep for code querying;
- AFL++ for fuzzing C code; and
- KLEE for symbolically executing C code.
Docker infrastructure
For the analysed application and the above tooling, the workshop provides a Docker Compose infrastructure with the following services/containers:
Ubuntu Portrait
- Service name:
portrait - Description: Demo Ubuntu Portrait instance
- Docker Compose profiles
portraitall
Dockerfilein theoss-fortressrepository:portrait/Dockerfile- Hosted image:
iosifache/oss_fortress_portrait:mainin GitHub Container Registry - Exposed ports:
8000for the web UI - User:
root - Credentials: N/A
- Relevant folders: N/A
OWASP Threat Dragon
- Service name:
owasp_threat_dragon - Description: OWASP Threat Dragon instance, accessible from
localhost - Docker Compose profiles
threat-modellingall
Dockerfilein theoss-fortressrepository: N/A- Hosted image:
owasp/threat-dragon:latestin Docker Hub - Exposed ports:
8001for the web UI - User:
root - Credentials: N/A
- Relevant folders: N/A
Coder
- Service name:
coder - Description: Coder instance, accessible from
localhost - Docker Compose profiles
threat-modellingall
Dockerfilein theoss-fortressrepository:tooling/coder/Dockerfile- Hosted image:
iosifache/oss_fortress_coder:mainin GitHub Container Registry - Exposed ports:
8002for the web UI - User:
coder - Credentials:
oss-fortressas the password for authenticating in the user interface - Relevant folders
/home/coder/codebasefor the Ubuntu Portrait codebase/home/coder/toolingfor the tooling-related information
Static analysers
- Service name:
static-analysers - Description: Ubuntu container with static analysers (Gitleaks, OSV-Scanner, flawfinder, Bandit, and Semgrep) installed
- Docker Compose profiles
static-analysisall
Dockerfilein theoss-fortressrepository:tooling/static-analysers/Dockerfile- Hosted image:
iosifache/oss_fortress_static_analysers:mainin GitHub Container Registry - Exposed ports: N/A
- User:
root - Credentials: N/A
- Relevant folders
/home/coder/codebasefor the Ubuntu Portrait codebase/home/coder/toolingfor the tooling-related information
AFL++
- Service name:
aflplusplus - Description: Container with AFL++ installed
- Docker Compose profiles
dynamic-analysisall
Dockerfilein theoss-fortressrepository:tooling/aflplusplus/Dockerfile- Hosted image:
iosifache/oss_fortress_aflplusplus:mainin GitHub Container Registry - Exposed ports: N/A
- User:
root - Credentials: N/A
- Relevant folders
/home/coder/codebasefor the Ubuntu Portrait codebase/home/coder/toolingfor the tooling-related information
KLEE
- Service name:
klee - Description: Container with KLEE installed
- Docker Compose profiles
dynamic-analysisall
Dockerfilein theoss-fortressrepository: N/A- Hosted image:
klee/klee:latestin GitHub Container Registry - Exposed ports: N/A
- User:
root - Credentials: N/A
- Relevant folders
/home/coder/codebasefor the Ubuntu Portrait codebase/home/coder/toolingfor the tooling-related information
Overview
The below infrastructure presents the recommended workflow for analysis, using the recommended tooling and Docker Compose services.